The Cost of Complacency: Why You Need a Comprehensive Data Loss Prevention Strategy
5 minute read
Imagine that you’ve just experienced a significant data breach. You’re worried about your job. Your bosses are worried about theirs.
The entire organization is frantic and they’re looking to you for answers.
“I thought we had policies in place to prevent this. What happened?”
“Why didn’t you catch this sooner?”
“Has this happened before?”
“How are you going to fix this?”
Despite more and more breaches making headlines every day, many organizations aren’t in a position to answer questions like these, let alone prevent, identify, or remediate any sort of data breach.
That must change.
And it starts with coming to terms with a hard truth: Your organization is at risk. While many may read this post and chalk it up to basic fear-mongering tactics, a quick search for the words “data breach” will hopefully convince you otherwise.
Even the world’s most secure organizations are affected by data loss. It’s unavoidable. But that doesn’t negate the need for preventative measures. Risk reduction is essential, and only by following best practices and implementing the right technology is it possible.
Download our latest whitepaper: Protecting Google Drive Data: 5 Critical Requirements for Data Loss Prevention.
Every Organization is a Target, Especially Small Businesses
Small businesses are attackers’ “favorite targets,” according to an Oct. 2015 SEC report, which called for small and midsize businesses to dedicate more time, money, and energy to prevent cybercrime. Approximately 75% of all spearphishing attacks (i.e. highly targeted attacks that usually involve executives or people handling sensitive information) are targeted at companies with less than 2,500 employees, with roughly 38% targeting companies with less than 250, according to a June 2015 Symantec Intelligence report.
Take UGI Utilities, a small Pennsylvania-based public utility company, for example. In January 2017, the names, social security numbers (SSNs), birthdates, addresses, salaries, and W2s of 1,600 employees were “acquired” via a data breach. Every affected employee is now (and for the rest of their lives) at risk of becoming an identity theft victim.
Financial organizations are the most common victims, making up 24% of confirmed breaches. Healthcare (15%), retail and accommodation (15%), and public sector entities (12%) rounded out the top four most commonly breached.
The Cost of a Data Breach
The average data breach costs $4 million, according to a 2016 Ponemon Cost of Data Breach Study. That’s why more and more attention and budget is allocated to the category of data management and protection. In fact, 57% of companies use two or more vendors to prevent data loss, according to the 2016 edition of the Global Data Protection Index.
Of course, there are direct financial consequences to data loss, but the indirect consequences are arguably even more significant. Deloitte lists 14 cyberattack business impact factors with the most costly being value of lost contract revenue, operational disruption, devaluation of trade name, and loss of intellectual property.
Further, employees affected by breaches are at a much greater risk of identity theft and falling victim to a phishing attack. “1 in 8 English consumers have experienced a breach of their digital healthcare data—more than half of those (56%) were victims of medical identity theft,” according to an Accenture 2017 Consumer Survey on Healthcare Cybersecurity and Digital Trust. This is a liability for the organization from which the data was stolen.
In 2015, 435,000 former Sony Pictures employees won a class-action lawsuit after being affected by a data breach. The settlement cost Sony an estimated $15 million and each employee was awarded $10,000.
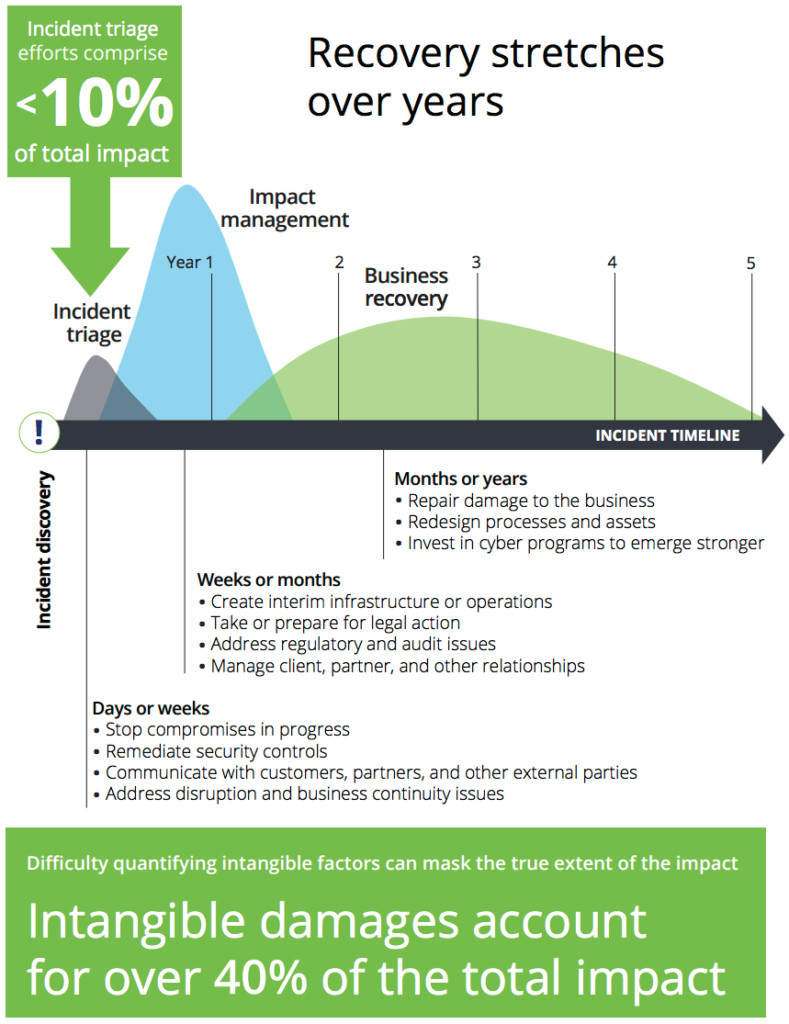
Image credit: Deloitte.
Sophisticated Attackers Make Detection Difficult
There are many intelligent people who are motivated by various factors, primarily money, to commit fraud or identity theft.
In late 2016, news surfaced of a hack affecting a midsize telecommunications and internet provider called Three UK. The hackers obtained personal information about 210,200 customers, according to The Telegraph. The attackers then used employee logins to carry out the hack, which enabled them to “trick the mobile company into sending them high-end upgrade handsets meant for customers.”
And it can take just minutes to compromise a domain, yet more than 75% of data loss incidents aren’t discovered for many days, according to a Sept. 2016 McAfee Labs Threat Report. Yahoo was affected by one of the largest data loss events in history (more than one billion accounts were exposed). They remained unaware for three years and the breach wasn’t even discovered by the Yahoo IT or security team.
To mitigate damage and remediate a breach quickly, you must detect the incident in the first place.
Middlesex Hospital is a great example of this. On October 9, 2015, the Middlesex IT team discovered that four of its employees had fallen victim to an email phishing scam. Unbeknownst to the victims, attackers secretly set up email forwarding rules. Even if the affected users followed recommended best practices and changed their passwords, the malicious email forwarding rules would continue to forward all emails to the hackers.
During a demo of BetterCloud, Middlesex Hospital decided to test one of BetterCloud’s email forwarding reports, which helps IT see all users who have forwarding rules in place, enabling them to identify where email is being forwarded to.
When the Middlesex Hospital IT team ran the report, they immediately noticed that emails were being forwarded to a suspicious address. “BetterCloud gave us the ability to identify exactly what happened that led to the breach,” said Shelton. The IT team immediately remediated the issue, removing the forwarding rules and resetting everyone’s passwords. Thankfully, the issue was identified within time to ensure no social security or credit card information was accessed.
Breaches Aren’t Always the Work of Attackers
While cyberattacks might get all the press, many data loss events are the result of human error and privilege misuse, which commonly takes months or years to detect without proper data loss prevention (DLP) in place, according to Verizon’s 2017 Data Breach Investigations Report.
These breaches can occur due to:
- Improper or incomplete offboarding: Companies often have former employees that still have access to company data, even years after exiting. Offboarding that takes hours, days, or even weeks to complete leaves companies vulnerable and is often a significant compliance issue.
- Accidental data disclosure: Misdelivery of information is far and away the primary form of human error, making up more than 50% of all error-related data breaches, according to Verizon’s 2017 report. With email autofill and human inattentiveness, it’s easy to understand how sensitive information escapes to the wrong person via email or accidental document sharing. Organizations should “focus on monitoring designed to capture (and prevent) data transfers” in real time, according to the Verizon report.
- Failure to revoke partner, contractor, or consultant access: The “freelance economy” is exploding. In fact, freelancers made up 35% of U.S. workers in 2016. Freelancers, along with partners, consultants, and other external parties are often granted limited time access to information. Many companies fail to revoke that access after the contract or partnership is severed.
- Lost or stolen devices: 95% of Americans own a cell phone, nearly 80% own a desktop or laptop computer, and more than 50% own a tablet, according to a 2017 Pew Research Center Mobile Fact Sheet. Losing or having a device stolen is common. Organizations without the ability to perform remote DLP actions, whether it’s wiping devices, resetting passwords, or even suspending accounts are vulnerable to a data breach.
- Malicious theft: In some cases, existing employees take advantage of the access they’re afforded. Many times, cases of malicious data theft have financial motivations, where employees intend to use company data for monetary gain or for a future competitive advantage, according to the Verizon report.
Combatting Complacency
Complacency is often the cause and catalyst for a data breach. Taking the “it-won’t-happen-to-me” approach is less expensive and less stressful, but it makes for a bigger headache later.
You need to take proactive action and take data loss head on. If you’re prepared and armed with the right technology, the likelihood of significant data loss undoubtedly decreases.
So how would you rank your ability to prevent, detect, and remediate a breach?
Before you go, download our whitepaper: Protecting Google Drive Data: 5 Critical Requirements for Data Loss Prevention.